Scaling up your Microsoft Sentinel Ingestion: Top Designs to Boost Your Security Game
🔥Scaling up your Microsoft Sentinel Ingestion: Top Designs to Boost Your Security Game🔥
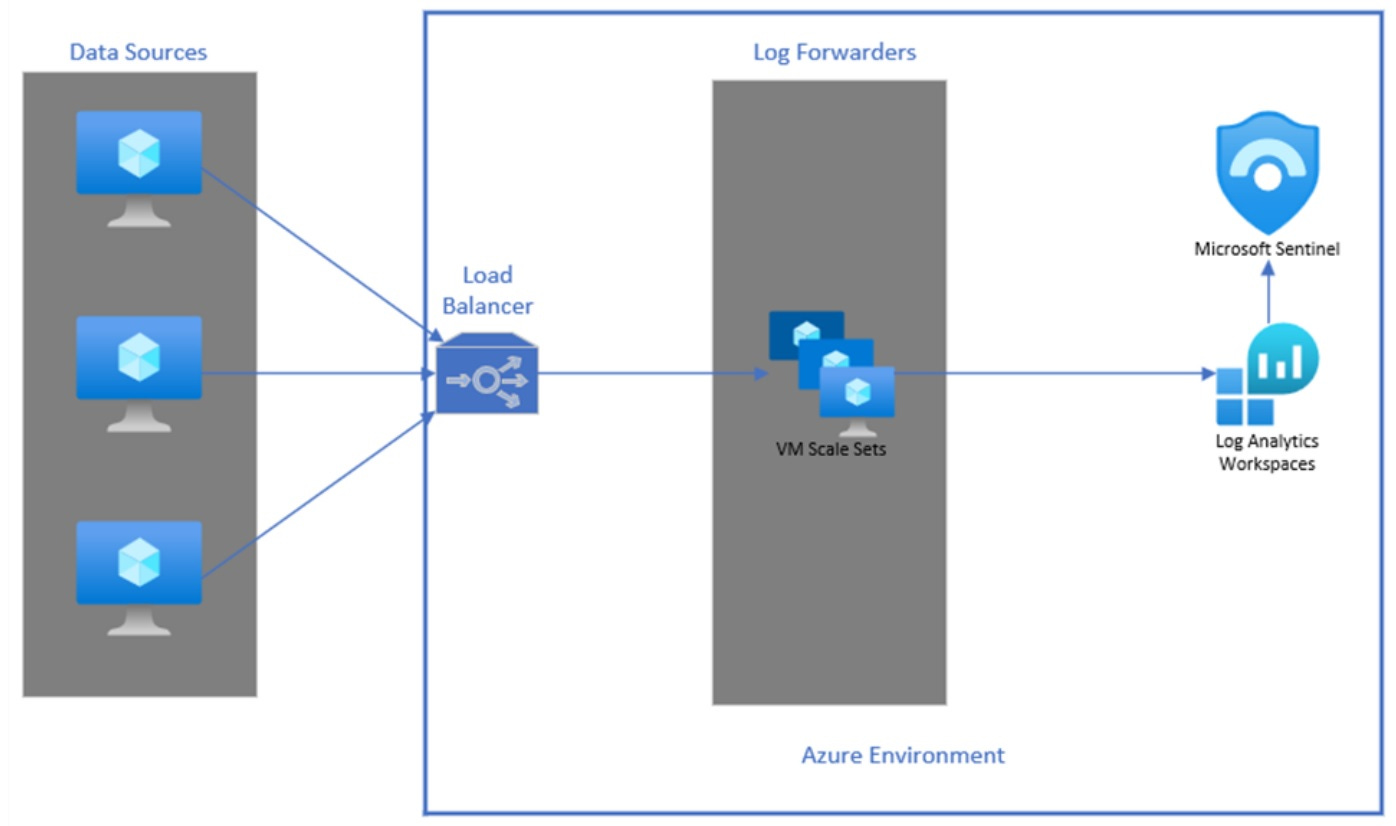
This blog post will present high-level insights on potential architecture designs to achieve a highly available and scalable ingestion pipeline for Microsoft Sentinel.
📝The post will cover the following components:
📌Load Balancer 📌Forwarder Systems 📌Data Sources (coming from endpoints)
📝The architectures can be classified into three main scenarios:
📌Azure-based: components for collection are within the Azure platform. (Load Balancer and VMSS in Azure - RECOMMENDED, Load Balancer and Forwarders in Azure - OPTIONAL) 📌Hybrid: one component resides outside of Azure. (Load Balancer Outside Azure/Forwarders in Azure) 📌Non-Azure: all components reside outside of Azure. (Load Balancer and Forwarders Outside Azure)
Each scenario above leverages the Azure Monitor Agent (AMA). AMA enables the usage of features that the Microsoft Monitoring Agent (MMA) provides and newer features such as ingestion time transformation, multi-homing, and more by using data collection rules (DCR) and data collection endpoints (DCE).
📝For additional information on how AMA handles different log sources:
📌For Syslog ingestion, please refer to: https://lnkd.in/dnnqpbJJ 📌For CEF ingestion, please refer to: https://lnkd.in/djXr4gDS 📌For Windows Event Forwarding, please refer to https://lnkd.in/dpzqv_k6
Want to learn more? 💡 📝https://lnkd.in/dCnDXuTs