🔥Public Preview alert: Configure Offline Security Intelligence Update for Microsoft Defender for Endpoint on Linux (preview)🔥
You can now update the security intelligence (also referred to as definitions or signatures in this document) on Linux endpoints with limited or no exposure to the internet using a local hosting server (Mirror server).
🔹Key benefits include:
☑️Ability to control and manage the frequency of signature downloads on the local server & the frequency at which endpoints pull the signatures from the local server.
☑️Adds an extra layer of protection & control as the downloaded signatures can be tested on a test device before being propagated to the entire fleet.
☑️Reduces network bandwidth as now only one local server will poll MS cloud to get the latest signatures on behalf of your entire fleet.
☑️Local server can run any of the three OS - Windows, Mac, Linux, and isn't required to install Defender for Endpoint.
☑️Provides the most up to date antivirus protection as signatures are always downloaded along with the latest compatible AV engine.
☑️In each iteration, signature with n-1 version is moved to a backup folder on the local server. If there's any issue with the latest signature, you can pull the n-1 signature version from the backup folder to your endpoints.
☑️On the rare occasion the offline update fails, you can also choose to fallback to online updates from Microsoft cloud(traditional method).
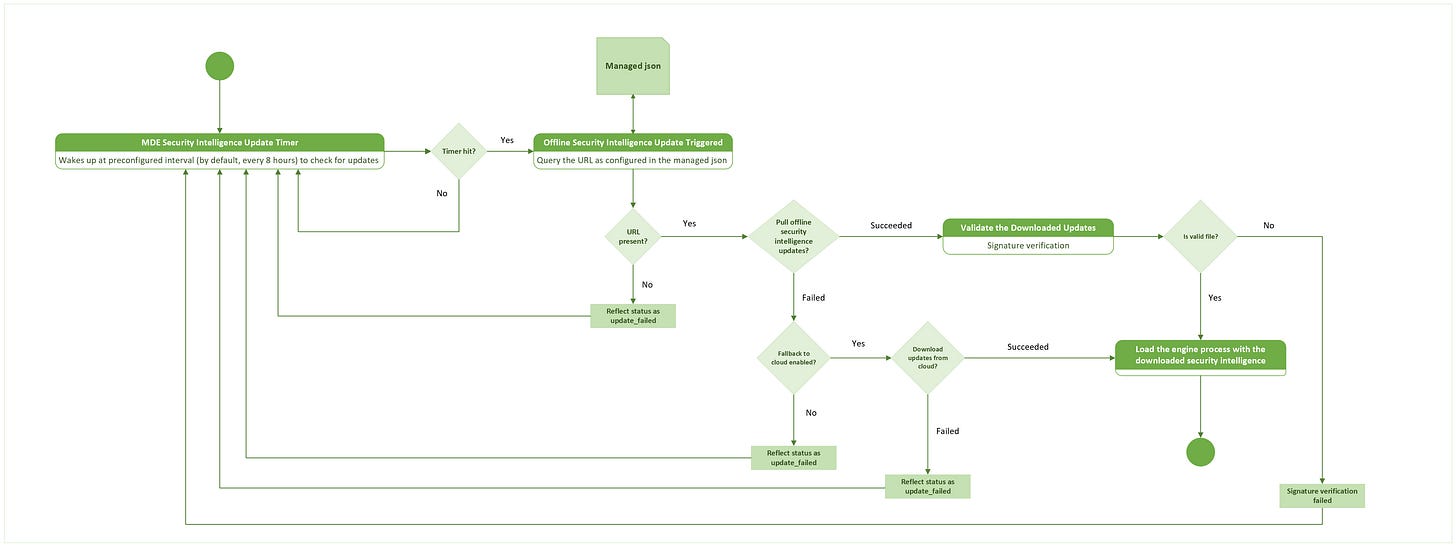
🔹How offline Security Intelligence Update works?
Organizations need to set up a Mirror Server, which is a local Web/NFS server that is reachable by the Microsoft cloud.
Signatures are downloaded from Microsoft Cloud on this Mirror Server by executing a script using cron job/task scheduler on the local server.
Linux endpoints running Defender for Endpoint pull the downloaded signatures from this Mirror Server at a user-defined time interval.
Signatures pulled on the Linux endpoints from the local server are first verified before loading it into the AV engine.
To trigger and configure the update process, update the managed config json file on the Linux endpoints.
The status of the update can be seen on the mdatp CLI.
Want to learn more?
Follow me on LinkedIn: José Lázaro Pinos | LinkedIn
#Microsoft #MicrosoftSecurity #MDE #DefenderForEndpoint #MSPartnerUK #SIEM #XDR #SOC #Linux #cybersecurity #MalwareProtection