Preventing Oversharing in Microsoft 365 Copilot: A Technical Blueprint for Readiness
As Microsoft 365 Copilot becomes more widely adopted, IT and security teams are being asked a crucial question:
Is your environment ready for AI to access and surface corporate data responsibly?
Microsoft’s Oversharing Risk Blueprint provides a tactical guide to help ensure Copilot doesn't unintentionally surface sensitive content due to excessive or legacy access permissions.
The Core Risk: Oversharing and Data Access
Copilot uses Microsoft Graph to ground responses in a user’s accessible content. If files or conversations are shared too broadly, they may be surfaced even if they weren’t intended to be widely available. This elevates the importance of precise access control and proactive governance.
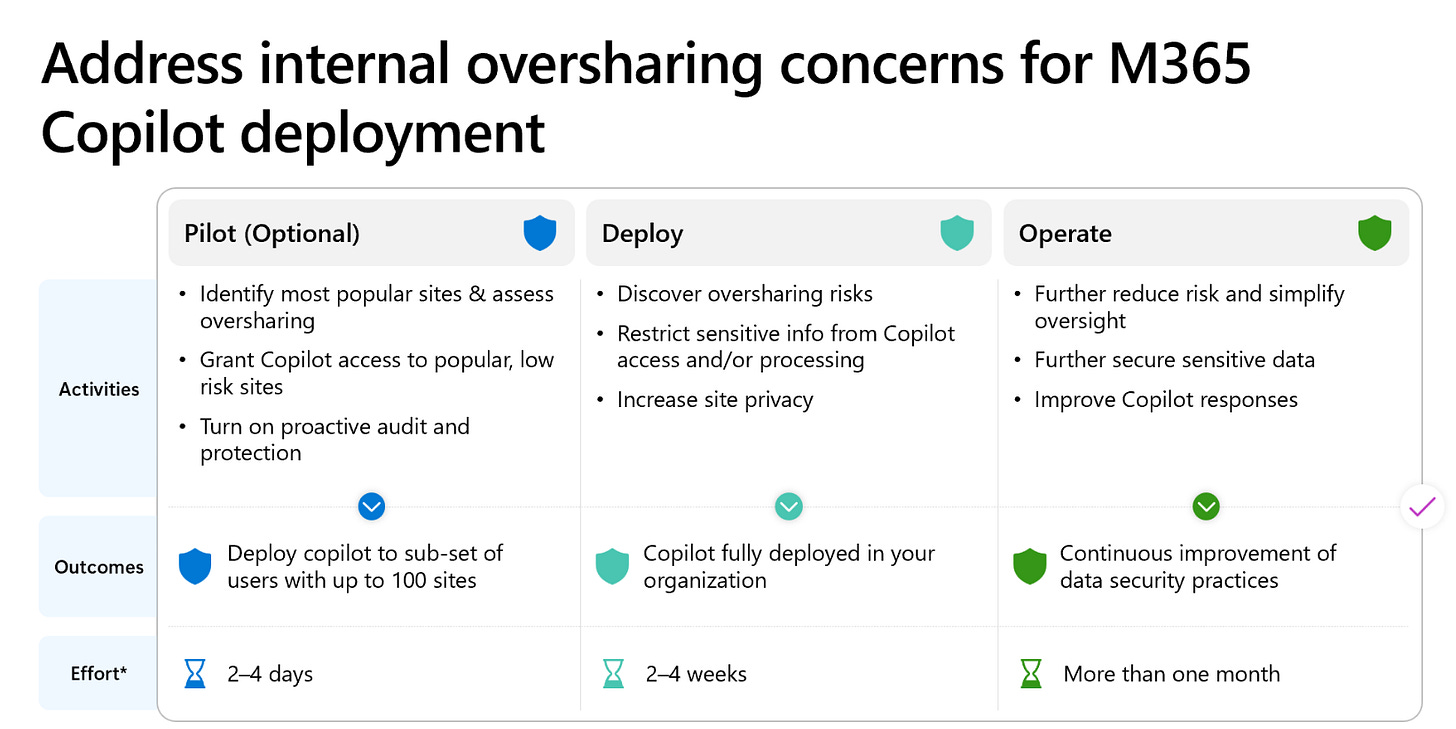
Microsoft’s Oversharing Blueprint: 4 Key Stages
1. Discover Sensitive Content That’s Overshared
Use Microsoft Purview to scan SharePoint and OneDrive for “Anyone” or “People in your organisation” links that expose content containing sensitive information.
2. Review and Assess Access
Audit permissions using Access Explorer. Focus on shared mailboxes, Teams repositories, and legacy file shares where access may be broader than intended.
3. Remediate and Harden the Environment
Update default link settings in SharePoint. Apply Sensitivity Labels, DLP, and Conditional Access to reduce exposure risk. Use Information Protection policies to manage what Copilot can surface.
4. Establish Ongoing Governance
Monitor permission changes and automate access reviews using Microsoft Entra and Entitlement Management. Align practices to Zero Trust principles.
Want to learn more?
📘 Full blueprint: https://learn.microsoft.com/en-us/copilot/microsoft-365/microsoft-365-copilot-blueprint-oversharing
#Microsoft #Cybersecurity #DataSecurity #Data #AI #Purview #SIEM #XDR #ShadowAI #MicrosoftSecurity #MSPartnerUK