🌐Introducing Microsoft Defender Threat Intelligence (MTDI) Interoperability with Microsoft 365 Defender🌐
Microsoft Defender Threat Intelligence is enhancing the way security analysts handle incident response, threat hunting, vulnerability management, and triage workflows by aggregating and enriching critical threat information in an easy-to-use interface.
🔹Defender TI is now integrated with Microsoft 365 Defender for licensed customers, combining its powerful threat intelligence capabilities with the advanced XDR functionality of M365D.
🔹Defender TI within M365 Defender ensures quick accessibility and easy reference, enabling analysts to swiftly gain context about threat actors and their tools and to launch advanced investigations into external threat infrastructure.
🔹Licensed users will benefit from the following features:
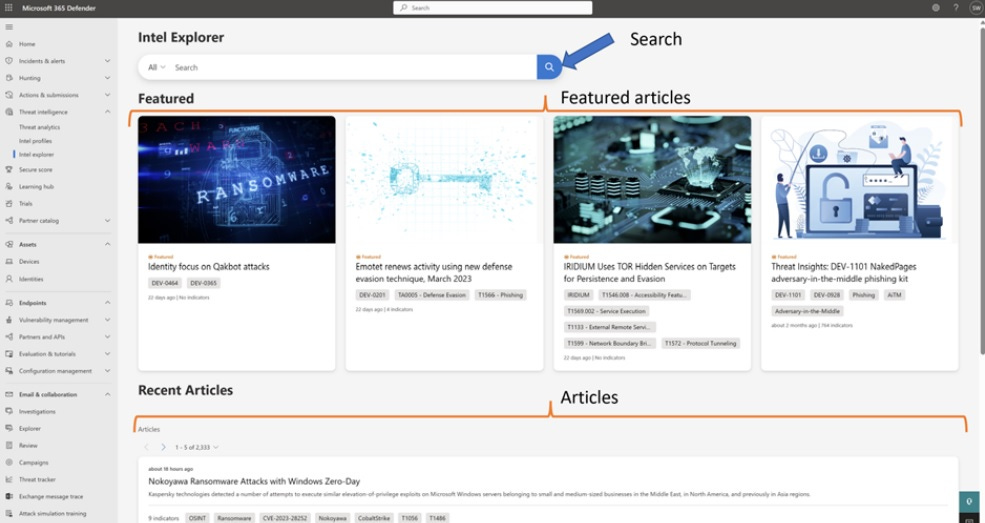
✔️Threat intelligence navigation blade tab: This new tab, along with threat analytics, has been moved under threat intelligence navigation.
✔️Intel Profiles: Comprehensive profiles detailing threat actors, their Indicators of Compromise (IOCs), and tools, tactics, and procedures (TTPs).
✔️Intel Explorer tab: This new tab enables pivots on Internet data to launch advanced investigations across Microsoft's continuously updated map of the entire Internet
🔹Here are two practical use cases for defenders using Defender TI within M365 Defender:
✔️Use Case: Advanced hunting with Defender TI IOCs against the logs and Events within Microsoft 365 Defender
In this scenario, we demonstrate how to compare identified IOCs from Defender TI, focusing on the Host Pairs data set related to the widely recognized "Franken-phish" Phish kit, and map this information to an advanced hunting query within M365 Defender. This approach can be replicated using IOCs from articles or Intel Profiles of threat actors and their associated tools.
✔️Use Case 2: M365 Defender Raw Event Detection
To demonstrate this use case, it is necessary to ingest M365 Defender raw events into Microsoft Sentinel through the M365 Defender Data connector. Furthermore, the user must also import Threat indicators from Defender TI by utilizing the new Defender TI Sentinel Data Connector. Following this, the user needs to execute TI correlation rules, which will compare the raw event tables of M365 Defender. Upon detecting a correlation, an incident will be generated in Microsoft Sentinel, which will incorporate the M365 Defender events and alerts.
❗Sign up for a trial:
📌MDTI Premium License trial: here
📌MDTI API License trial: here
Want to learn more? See full article with the use cases here: